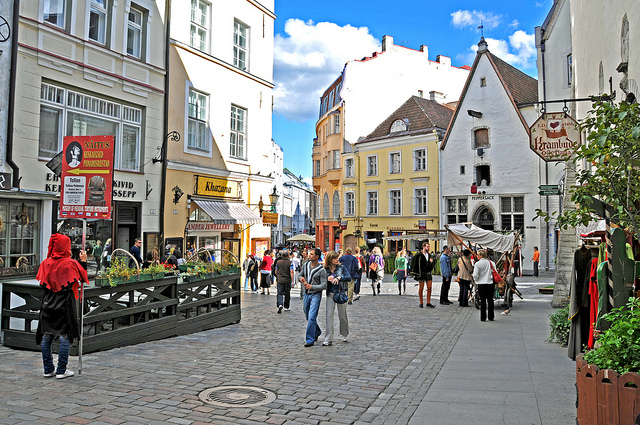Cyber Attacks and Espionage in the Digital Age
“Well that’s because [Putin] would rather have a puppet as president of the United States,” Democratic Party nominee Hillary Clinton fiercely told the audience at the third presidential debate in Las Vegas.
“You’re the puppet!” her rival, GOP nominee Donald Trump, retorted childishly.
For most Americans watching the final presidential debate on October 19, the 2016 election had devolved into a game of a “he-said, she-said” that infants would play on any given car ride with their parents. Yet buried within the tired political rhetoric was the heart of a serious security issue: hacking and cyber warfare.
Clinton’s charge that Trump is a puppet of Russian President Vladimir Putin, while at this point impossible to prove, derived from the now infamous WikiLeaks publication that showcased foul play on the part of her party during the nomination contest earlier this year.
On July 22, three days before the DNC planned to formally anoint Clinton as its party’s presidential nominee, more than 19,000 emails from the party’s committee were leaked to the public. Inside the trove of stolen digital information, the American public learned that several of the committee members, including its Chair, Debbie Wasserman Schultz, favored the nomination of Hillary Clinton over Senator Bernie Sanders when they were supposed to be neutral.
The emails released by WikiLeaks confirmed to many Sanders supporters what they had suspected throughout the six-month primary battle: the Democratic party officials had circled their wagons around Clinton and never took the Vermont senator seriously as a potential nominee. Schultz later resigned her post as the fallout quickly spread over the convention and the race itself.
“Between super delegates and Deborah Wasserman Schultz, [Sanders] never had a chance,” Trump blasted during the second presidential debate in October.
Clinton responded by deflecting these charges and accusing the Russian government of orchestrating the DNC hack, which then allegedly turned over the information to WikiLeaks for publication. As Clinton and her campaign staff have explained to voters, the Russian government secretly supports the Trump campaign and is actively working to turn public opinion against Clinton. Russia’s motivation in such a scheme isn’t hard to decipher as Trump has repeatedly criticized the Obama Administration’s conflicting relationship with Putin while simultaneously threatening to have the US leave NATO if he is elected.
IN THE PHOTO:GOP Nominee Donald Trump squared off with Democratic Nominee Hillary Clinton at the third presidential debate in Las Vegas. State-sponsored hacking has been a major talking point throughout the campaign. PHOTO CREDIT: Bill B/Flickr
“This [hack] has come from the highest levels of the Russian government,” Clinton confidently proclaimed at the third presidential debate. “Clearly from Putin himself in an effort, as 17 of our intelligence agencies have confirmed, to influence our election.”
US intelligence agencies have in fact only gone as far as declaring that they have “high confidence” that the Russian government was behind the hack, and without any of the government’s evidence available for review, it can’t be made for certain that Russia was responsible.
Russian officials nevertheless continue to deny the accusations. Kremlin spokesperson Dmitry Peskov has called the charges “so absurd that it borders on total stupidity.”
It remains unlikely that we’ll determine whether Russia was indeed responsible for the DNC hack before Americans head to the polls on November 8. However, whoever ultimately moves into the White House early next year will need to confront cyber security threats such as this one.
Since the turn of the last century, the international community has witnessed numerous cases of state-sponsored cyber attacks and cyber espionage. As some experts have documented, well-targeted cyber attacks now have the potential to cripple an entire nation’s telecommunications infrastructure. As it turns out, the DNC hack was just a thumb prick compared to the havoc that cyber warfare could ultimately unleash. Good thing that there are well-versed cyber companies, such as the ones on https://indexsy.com/best-cybersecurity-companies/, that can prevent or safeguard against such ill-natured cyber attacks.
The preponderance of cyber attacks has been only been increasing by the years and has accentuated on the importance of more secure and impenetrable security networks. That has, concomitantly, created vacancies for people skilled in tackling such malicious attacks. People looking to get into cyber security should consider taking a course in such to get a solid foundation of knowledge under their belt before applying for jobs.
Denial-of-Service
On October 21, Americans living on the east coast of the country awoke to discover that their computers were unable to access their favorite websites. Sites such as Twitter, Netflix, Spotify and The New York Times were sporadically blocked or had their pages slowed down to the point where they were of no use for visitors.
Around 7 A.M. that morning, the cloud-based Internet Performance Management company Dyn had come under a distributed denial-of-service (DDOS) attack. Throughout the day, hackers overwhelmed Dyn’s servers through hundreds of thousands of internet connected devices. Dyn, which hosts a Domain Name System, was unable to keep up with the hackers, and in turn the company’s clients saw their web pages stumble and collapse.
Related Article: “DECONSTRUCTING EMPATHY IN THE DIGITAL AGE“
Although Dyn had secured its servers by the end of the day, the attack was a reminder of the power that hackers can wield over American internet access. Over that following weekend, politicians voiced concern that hackers could disrupt the upcoming election by interfering with internet ballots, which Americans living abroad and active service personnel rely upon every November.
The most alarming statistic, however, came from Verisign, which acts as a registrar for websites. In its recent report, the company found that between April and June, DDOS attacks had risen 75 percent from the same period a year ago. In addition, hackers had begun to use different methods to attack servers, with the average hack being twice as large as before.
The United States is not alone when it comes to widespread DDOS hacks; almost ten years ago, Estonia was forced to block all internet access across its borders after foreign hackers brought havoc upon its telecommunications.
Starting on April 26, 2007, hackers infected the Estonian government’s websites with an onslaught of DOS viruses, blocking access for government employees and civilians. Within the first week, the DOS outbreak infected Estonian media outlets and universities. On May 9, the hackers unleashed their heaviest bombardment upon the country’s banking systems.
Within 24 hours, Hansabank, Estonia’s largest financial institution, was forced to cease its internet operations entirely. Estonians were prevented from using ATMs and other online banking practices, which is considerable when 97 percent of all Estonian banking transactions occurred online at the time. Estonians outside of the country quickly learned that their debit cards were useless as their banks had severed internet connection beyond its borders.
Only after barricading itself from foreign interference did the cyber attacks ground to a halt after three weeks of confusion and frustration. Although only one person was ultimately arrested and charged in the subsequent investigation, Estonian law officials were confident that the DOS attacks were the result of the government’s decision to remove a Soviet war monument. It was then presumed that the cyber attacks were a new form of political protest by pro-Russian “hacktivists.”
IN THE PHOTO:Tallinn, Estonia. The Baltic nation was forced to block all foreign telecommunications after a DDOS attack in 2007. PHOTO CREDIT: Dennis J./Flickr.
While a cyber war of this scale would result in only minimal damage to a country as a large as the United States, cyber security analysts across the globe nonetheless took great pains to fully examine the Estonian case.
The International Affairs Review, for instance, found that a robust cyber attack on any sector of the United States’ SCADA systems has the potential to lower the quality of life for American citizens as automated regulatory systems fail. Any disruption of SCADA would in turn disrupt utilities such as water, electricity and mass transit, potentially endangering the lives of millions of Americans.
“An Advanced Persistent Threat”
For most Americans, however, cyber warfare remains primarily a national security issue and not a doomsday scenario. In fact, up to this point, most state-sponsored cyber attacks have been implemented for espionage as rising global powers work to steal classified information that can give them any military or economic advantage. One such state actor is China, which has for the past 15 years repeatedly infiltrated American servers in both the private and public sectors, stealing tens of millions of classified information.
In February of 2013, the American computer security firm Mandiant issued a 60-page report that detailed Chinese hacking activities since 2006. Mandiant found that the PLA, specifically PLA Unit 61398, had intruded into 20 major sectors, including defense contractors and infrastructure systems. The hackers would, on average, hide within the system for a year, looting information that the unit believed was useful for its military and economy.
A month later, National Security Advisor Thomas Donilon went before the Asia Society and called on China to recognize and investigate the hacking issue and the threat that it entailed. “From the president on down,” Donilon said. “This has become a key point of concern and discussion with China at all levels of our governments and it will continue to be. The United States will do all it must to protect our national networks, critical infrastructure and our valuable public and private-sector property.”
As early as 2001, the Chinese government has sponsored and trained hackers in the arts of cyber warfare. By establishing “information-security research” departments in more than 50 Chinese universities, the government has helped develop an entire generation of hackers capable of infiltrating some of the most secure networks in the world. That same year, in an operation later dubbed Titan Rain by US officials, Chinese hackers began a cyber campaign that would go on to gain access to a broad spectrum of Western servers, including military, corporate and government networks.
Five years later, Chinese hacks had become an “advanced persistent threat,” according to Colonel Gregory Rattray, group commander in the Air Force Information Warfare Center. In one major hack, Chinese hackers broke into the Lockheed Martin network and stole millions of documents on the company’s F-35 Joint Strike Fighter jet.
IN THE PHOTO:Chinese soldiers at Tiananmen square. The PLA has regularly infiltrated Western servers since 2001. PHOTO CREDIT: Peter M./Flickr
Despite the high valued treasure trove of stolen documents, the Chinese hacking devices are remarkably simple. According to The Atlantic, a “typical” Chinese hacking tool is the “Remote Access Trojan” (RAT), which is activated when an employee clicks an email attachment that is covertly sent from the hackers themselves. Over a five-year period, the anti-virus firm McAfee informed the US government that the Chinese had used RATs to steal data from more than 70 government agencies and private companies in 14 countries.
As Colonel Rattray noted, the Chinese hacks will continue to plague Western servers as they have for much of the present century. It then falls on these players to shore up a defensive strategy against hacking, which as it turns out, requires some foul play hacking of its own.
If You Can’t Beat Them…
It is now abundantly clear to most in the private and public sector that cyber attacks are a clear and present danger, though a bulletproof firewall has yet to materialize.
Writing for the Harvard Business Review, Greg Ball doesn’t believe that it’s possible to build any such firewall in the first place. “Even if it were possible to build a wall that’s 100 percent secure, it wouldn’t begin to protect the rapidly growing amount of sensitive data that flows outside the firewall through devices and systems beyond the company’s direct control.”
The focus of Ball’s October article was on corporate measures to prevent cyber theft and other attacks, but his views can be extended to the public sector as well.
As far as the American public is concerned, the United States government has done little to prevent cyber attacks such as the DDOS strike in October or those coming out of China. President Obama, for example, has only issued a vague executive order calling for improved information sharing between the government and industry leaders. “We all know what we need to do,” Obama told members of the tech industry in Silicon Valley. “We have to build stronger defenses and disrupt more attacks.”
IN THE PHOTO: President Obama at Hannover Messe 2016. Obama issued an executive order calling on the private and public sectors to unite against cyber attacks. PHOTO CREDIT: US Department of Commerce/Flickr.
It wasn’t until a Russian anti-virus firm revealed the NSA’s own cyber warfare program that the public then learned that the government’s role in countering cyber threats lay on the internet battlefield.
The company, Kaspersky, revealed to the public that the US government has overseen what Wired magazine has branded as a “cyber Manhattan Project.” Beginning in 2001, the NSA’s Tailored Access Operations unit, or “Equation Group” as Kaspersky calls it, has engineered six different forms of malware, with each device designed to infiltrate and ultimately take control of suspicious computers.
“The group is unique in almost in every aspect of their activities,” Kaspersky said. “They use tools that are very complicated and expensive to develop, in order to infect victims, retrieve data, and hide activity in an outstandingly professional way.”
These tools include update mechanisms, dozens of plug-ins, a self-destruct function, code obfuscation as well as hundreds of phony websites that act as “command-and-control.” Kaspersky also identified a malware plug-in that reprograms a hard drive’s firmware and can even survive a disc wipe. Until now, that tactic was believed to only be possible in labs under the supervision of computer scientists, according to Wired.
For some, the NSA’s cyber warfare program is another existential threat to American privacy. Other critics are not so sure, however.
“If the US spends a billion dollars in cyber defense, it will still be vulnerable,” wrote Kevin Paulsen for Wired magazine. “But spend it on cyber attack and you get the most advanced computer espionage and sabotage tools that history has ever seen.”
The best defense, Paulsen contends, is a good offense, in which case Americans can take some comfort in the fact that the NSA is doing all it can to win a cyber war if one were to erupt in the future.
Thus a Promethean dilemma materializes: the internet provides us with limitless access to information while at the same time connecting us to the world at large, but only at the price that hackers and government agencies will forever hover over our keyboards, potentially threatening the very tools and privacy that we have come to depend upon.
Perhaps no one is safe after all.
Recommended Reading: “US ACCUSES RUSSIA OF CYBER ATTACKS“